If you’ve followed the news today, you’ve likely already seen reports of a new virulent ransomware variant spreading across the globe. Petya 2.0 (also called NotPetya by some researchers) has already claimed victims across Europe, Russia and the US. Known victims include Maersk, healthcare facilities in Pittsburgh, and several banks in Ukraine.
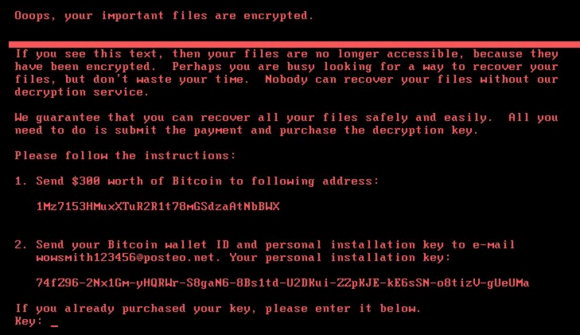
Petya 2.0 works similarly to its cousin, the original Petya seen last year, by encrypting the Master Boot Record (MBR) on the victim’s computer rather than individual files. Encrypting the MBR effectively locks the victim out of their computer entirely until the ransom is paid and a decryption key is entered. Instead of booting into Windows, the computer boots to a ransom note instructing the victim to send $300 in Bitcoin to a wallet address and then email a unique ID to the attacker to receive a decryption key.
By following the transaction’s on attacker’s bitcoin wallet address, we see several thousand dollars in ransom already paid by victims hoping to recover access to their computers. Unfortunately, the email hosting provider for the email address used in the ransom note has locked the attacker’s account which means even if a victim pays the ransom, there is no way for them to receive their decryption key.
Petya 2.0 is primarily distributed using a fake order confirmation attachment on a phishing email. After it infects the initial victim but before encryption, Petya 2.0 exploits the same EternalBlue (MS17-010) vulnerabilities as the WannaCry ransomware variant to move laterally through the victim’s network and infect other systems. Petya 2.0 also appears to leverage legitimate Windows tools PSExec and WMIC to infect Windows machines that are already patched for the EternalBlue vulnerabilities.
Researchers have discovered several ways to potentially halt the MBR encryption process on an infected system. Upon initial execution, Petya 2.0 schedules a system reboot after 1 hour. After the reboot, Petya 2.0 halts the Windows boot process and instead loads its own code to encrypt the MBR. If the victim powers off an infected computer before the encryption process completes, they can potentially save the MBR, allowing them to back up files to a different system before wiping the infected computer.
Additionally, researchers have discovered a potential kill switch within Petya 2.0. During Petya 2.0’s execution, it checks for the existence of a file “C:\Windows\perfc” (no file extension). If the file exists, execution is halted. An administrator can create a file at that location to prevent Petya 2.0 from executing and encrypting their system.
Petya 2.0 further highlights the need for keeping systems patched with the latest security updates. Furthermore, businesses should ensure their employees are educated on spotting phishing emails to prevent Petya 2.0 and other ransomware from gaining a foothold in their networks.
The recent string of ransomware attacks, including Petya 2.0 and WannaCry, brings to light just how critical adoption of a layered approach to security is. For example, as our Q1 Internet Security Report pointed out, 38% of malware gets past legacy AV, this is why services like IPS, sandboxing, and detection and response are so critical. No single solution is going to provide 100% coverage. As evidenced, WatchGuard customers leveraging Total Security Suite were protected from both WannaCry and Petya 2.0, but both attacks were blocked using a different combination of services.
For more information on how WatchGuard blocked this attack and for further tips on preventing Petya 2.0 infections. WatchGuard customers should see our Petya 2.0 Knowledge Base article.
—Marc Laliberte