Though not the biggest on record, today’s Patch Day is no slouch.
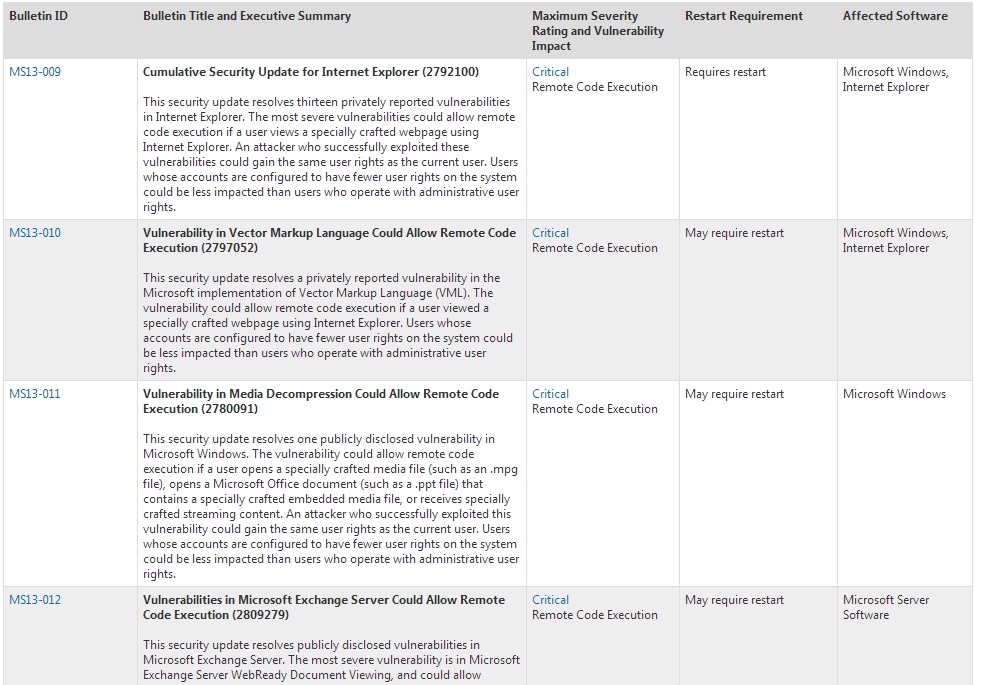
As expected, Microsoft released a dozen security bulletins, fixing 57 vulnerabilities that affect a range of their software, including:
- Windows (and its components)
- .NET Framework
- Internet Explorer (IE)
- Exchange Server
- Fast Search Server 2010
According to the summary alert, Microsoft rates five of the bulletins as Critical, which typically means remote attackers can exploit them to gain control of affected computers (usually with little to no user interaction). In general, I recommend you apply these Critical updates first.
In particular, I’d start with the two IE updates since attackers often target users with drive-by download attacks. Also, jump on the Exchange server update immediately, as it fixes an issue attackers could easily exploit with a specially crafted email and attachment—not to mention, your email server is a pretty critical asset.
Though not as serious as other issues, one of Microsoft’s alerts describes a Windows TCP/IP Denial of Service vulnerability, which it sounds like attackers could exploit with a single malicious packet. I haven’t seen this sort of “Ping of Death”-like DoS vulnerability in a while.
As always, I recommend you test the updates before deploying them to a production environment. If you don’t have time or resources to test all of them, at least try to test the server-related updates.
As an aside, WatchGuard’s IPS signature team gets early warning about Patch Day, and will release a new signature update that detects some of the described issues shortly. The have developed signatures for the following Patch Day-related issues:
- CVE-2013-0015
- CVE-2013-0018
- CVE-2013-0019
- CVE-2013-0020
- CVE-2013-0021
- CVE-2013-0022
- CVE-2013-0023
- CVE-2013-0024
- CVE-2013-0025
- CVE-2013-0026
- CVE-2013-0027
- CVE-2013-0028
- CVE-2013-0029
- CVE-2013-0030
- CVE-2013-0077
- CVE-2013-1313
We’ll post consolidated alerts throughout the day, sharing more details about these bulletins and updates. Stay tuned. — Corey Nachreiner, CISSP (@SecAdept)

After studying this material, I have some notes:
– MS13-010 (covered vulnerability in VML-parser (Vector Markup Language)).
VML-parser, used by Internet Explorer, can not be disabled or switched off in Windows…
– MS13-013. Just curious. Didn’t know and had no idea, that Microsoft Exchange Server 2007/2010 includes custom implementation of the “Oracle Outside In libraries” (technology to transform and manage content of unstructured files).
Sorry, my mistype 🙂 MS 13-012 is the correct number for Microsoft Exchange Server vulnerability