Automatically preventing all traffic from hosts that attempt to connect to blocked ports can help prevent further malicious actions from those IP addresses as explained in Auto-Blocking Suspicious Hosts Found in Traffic Logs. After posting that article, one WatchGuard customer sent me a note about using the auto-block feature to help prevent DDoS attacks. By reducing the processing time for known bad hosts as explained in the last post, the firewall has more resources left to handle other requests.
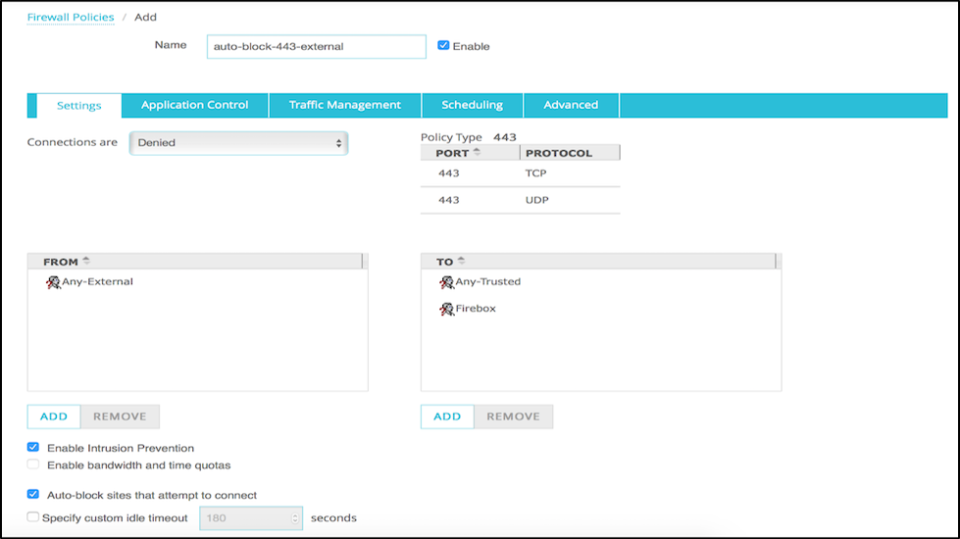
Some readers asked how to auto-block a port for external traffic only. For example, some environments need port 443 to be open on all or part of the network inside the company, but any attempt to connect to that port from an external source should be auto-blocked. In that case, instead of blocking every connection attempt on port 443 automatically, create a policy which denies external traffic on port 443 to the Firebox and Any-Trusted aliases. The “Any-Trusted” alias covers networks defined on, or routed behind the trusted (internal) interfaces. The “Firebox” alias covers any IP address assigned to the Firebox, public or private. Then check the box labeled “Auto-block sites that connect to attempt to connect.”
I suggested this in the comments of my last blog post and someone tried it out. As soon as he turned on the rule, the logs filled with hundreds of auto-blocked IP addresses.
If a valid host accidentally connects to a port in the policy above, the Firebox will add that host to the auto-block list along with all the malicious hosts. This may be a good thing because a presentation at Def Con talked about the potential threat from internal DDoS attacks. However, If a firewall administrator wants to ensure certain hosts that connect to a denied port are not completely blocked, create a separate deny rule with auto-block turned off for those IP addresses. Make sure the rule with auto-block off is above the rule with auto-block on in the policy list. — Teri Radichel (@teriradichel)