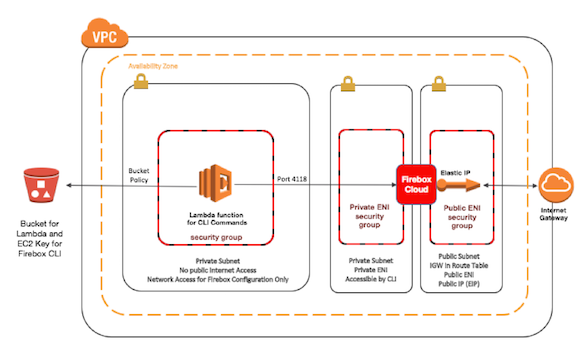
The last Secplicity blog post in this series on cloud security described the security benefits of CloudFormation for automated deployments. CloudFormation can deploy security appliances in AWS accounts that help protect applications and data in cloud environments.
UTM (or Next-Gen Firewall) on AWS
Deploying a WatchGuard Firebox Cloud is one way to increase security in an AWS account. A WatchGuard Firebox Cloud is a virtual version of the WatchGuard hardware UTM (unified threat management) device. A UTM combines several security services that work together to block, remove and report on threats in an environment. In addition to standard firewall protections, the WatchGuard Total Security license includes things like APT Blocker, Data Loss Prevention (DLP), Intrusion Prevention Service (IPS) and more. The Firebox Cloud can also create a VPN or encrypted channel for traffic sent to and from other networks.
At a high level, the code creates the following resources:
The Code
The code described in this blog post exists in the FireboxCloudAutomation GitHub repository. GitHub is a way to publicly share code with other people on the Internet. GitHub users can also create private repositories. The first file you will see when you click the link is the README.md file which offers some information about the repository. The code should be simple enough to run for someone new to AWS and Firebox Cloud by following the instructions in the README.md file. If new to AWS, refer to the AWS documentation to learn more about AWS or AWS Networking.
Click on the code link to drill down into the files contained in the repository. The wiki offers details about the code, resources it creates and updates as the code evolves.
Before You Begin: Set Up Your Environment
Start by following the instructions in the readme file under “Before Your Run This Script”. This section has links that explain how to set up an AWS account, enable MFA, install the required tools, and download the code. Once your AWS environment is ready, you will be able to easily set up a Firebox Cloud instance in your account.
Run the Code
After executing the git clone command as explained in the set-up instructions, the same code will exist on the local machine. You will be able to navigate to the folder containing the code and see the same files that exist in the GitHub repository.
To run the code, follow these steps.
Open a terminal window and navigate to the code directory. You can type pwd to show the current path which should end with /FireboxCloudAutomation/code. If you type ls you will see the following files when you are in the correct directory.
Type ./run.sh and hit enter.
The code will display the region in the AWS CLI configuration. The screen shot below shows me that executing the script with this configuration will deploy resources in the us-west-2 region which is in the state of Oregon in the US. Following the region information, the script displays options it supports.
Type 1 for Create/Update and hit enter.
The script will retrieve the input values needed to execute the script. The script will list out the Firebox AMIs that are active in your account. If you followed the environment setup instructions in the README.md file you should see a list of AMIs. Note that the AMIs are region-specific.
After retrieving the required information, the script will display all the default values. Review the values and type “Y” to use these values. If you need to change any of the values just type enter and a prompt will appear to enter each value. You can hit enter to use the default or type something different. In most cases the defaults will work except for the CIDR blocks. If subnets exist that use or overlap with these CIDR blocks in your account, you will need to choose alternate CIDR blocks. Also note that to run this script you need permission to create all the resources contained within this script, including networking, policies, KMS and EC2 keys, and IAM roles.
Certain actions in the script require an MFA token. Following the environment set-up steps in the readme adds MFA (multi-factor authentication) to your AWS user account. When a user with MFA enabled logs into the AWS console, after logging in with the correct user name and password, that user will have to enter a code. The device registered during MFA setup will constantly generate new codes. For example, Google Authenticator running on an iPhone looks like the screen shot below. The picture shows codes for two different AWS accounts.
Enter the token for the user name and account (greyed out above) used to execute the code. The code will create a session that will last for 12 hours, so no need to enter the token again until the session expires.
At this point, the code executes CloudFormation templates to create resources in your AWS account. The terminal window will list details about commands executed.
View the CloudFormation stacks and resources created by logging into the AWS console as explained in the prior Secplicity post on CloudFormation.
If the script completes successfully you’ll see “Done” at the end.
Go to the EC2 Dashboard in the AWS Console and you’ll see the Firebox Cloud AWS EC2 instance (a virtual machine running on the AWS Cloud) and its public IP address.
You can use that IP address to navigate to the Firebox Web UI at http://x.x.x.x:8080 where x.x.x.x is the IP address for the Firebox shown in blue in the above screen shot. You will have a different IP address in your own account.
If there is an error while running the create code, you can simply re-run the code in most cases. Manual updates in the console and certain code changes can cause this re-run process to fail. In a production environment, you would want to test the code and re-run it in some environment other than production to make sure it works correctly before running in production.
Run the script and select the Delete command to remove the resources (and avoid paying for them when not in use).
Hopefully this example will help you become familiar with automated deployments of security appliances such as a WatchGuard Firebox Cloud in your AWS account. — Teri Radichel (@teriradichel)