Using a risk model based on security statistics is a valid and useful approach to defending against cyber attacks. A company can decide that if one type of attack is affecting a large percentage of companies, then chances are, they may be next. The company can take steps to defend against that attack. However, sometimes past statistics are not enough and can be … [Read more...]
DNSMasq Vulnerabilities Affect Network Devices, Microservices, and More
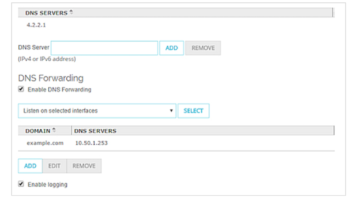
On October 2nd, the Google security blog announced several vulnerabilities in a piece of software called DNSMasq, which offers DNS forwarding and DHCP services for small computer networks. Days before, IT Briefcase published an article I wrote about indicators of compromise in DNS logs. The article explains that an exploited DNS server may offer the path from an external to an … [Read more...]
Auto-Blocking Suspicious Hosts Found in Traffic Logs
Many attackers and hosts infected with malware try to infect other hosts by scanning networks for open ports exposed to the Internet. After finding an open port, a malicious third party will attack software running on that port using known vulnerabilities. These published software flaws can cause damage or allow unauthorized access to hosts and networks. Often vendors publish … [Read more...]
How to Automate Deployment of a WatchGuard Firebox Cloud on AWS
The last Secplicity blog post in this series on cloud security described the security benefits of CloudFormation for automated deployments. CloudFormation can deploy security appliances in AWS accounts that help protect applications and data in cloud environments. UTM (or Next-Gen Firewall) on AWS Deploying a WatchGuard Firebox Cloud is one way to increase security in an … [Read more...]