Last week, researchers found a new crypto-ransomware variant that gave its encrypted files a .locked extension, which seems similar to the Locky ransomware. For a short time, this caused some to assume that this was a new Locky variant, and for reasons I’ll get to later, it gave them hope that we might be able to decrypt Locky files. Since I recently shared my own experiences with Locky, and how well WatchGuard appliances stop it, I was interested in this new variant and wanted to dispel any false impressions.
Unfortunately, those hopeful people’s first impressions proved wrong. This new sample is not connected to Locky. Nevertheless, it’s a great illustration that not every piece of ransomware succeeds. This sample didn’t survive long enough to get a widely known name, although it infected around 700 victims in one day.
Like other crypto-ransomware, this sample encodes files using AES encryption, and as I mentioned before, adds the .locked extension, which is likely why people confused it with Locky. However, remember that Locky uses the .locky extensions, not .locked.
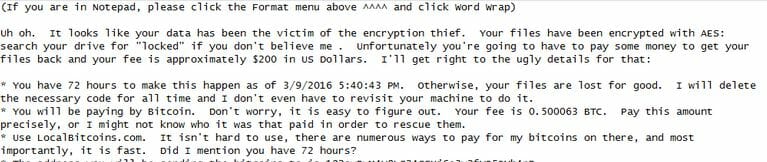
So why were people hopeful that we might decrypt Locky files? A few hours after the first infections, a person named Utku Sen published the decryption keys for the affected victims. How was this possible?
It turns out Sen is a researcher who developed a proof-of-concept (PoC) file-encryption project called EDA2. This new ransomware’s authors used code from the EDA2 project to encrypt their victims’ files. Fortunately for the victims, Sen built a backdoor into EDA2 to avoid malicious actors from abusing his encryption project for nefarious purposes. He simply used his backdoor to provide the decryption keys to all the victims. A few hours later, the Command & Control (C&C) servers for this crypto ransomware disappeared, probably because the attackers accepted their defeat.
Ransomware isn’t always devastating. In this case, quick help was made available to recover the victims’ files. However, not all cases are this easy. Other variants like Locky, Cryptowall, and newer TeslaCrypt variants use well-crafted encryption mechanisms, which are near impossible to crack on today’s computers in a reasonable amount of time. This is why you should keep your shields up, and use a combination of security services that offer layered protection against today’s even evolving threats.
Additionally, I highly recommend you create regular backups of your data, and keep them in a safe and unconnected place. That way you can still restore your important data in worst case. One note; you may also want to backup any files that might get encrypted by ransomware. There’s no guarantee, but we have seen decryption tools for other crypto-malware variants published months after the first infections (e.g. Tesla Crypt 2). — Jonas Spieckermann

Leave a Reply