Severity: High
Summary:
- These vulnerabilities affect: Adobe Flash Player and ColdFusion
- How an attacker exploits them: Multiple vectors of attack, including enticing your users to open malicious files or into visiting specially crafted web sites
- Impact: Various results; in the worst case, an attacker can gain complete control of your computer
- What to do: Install the appropriate Adobe patches immediately, or let Adobe’s updater do it for you.
Exposure:
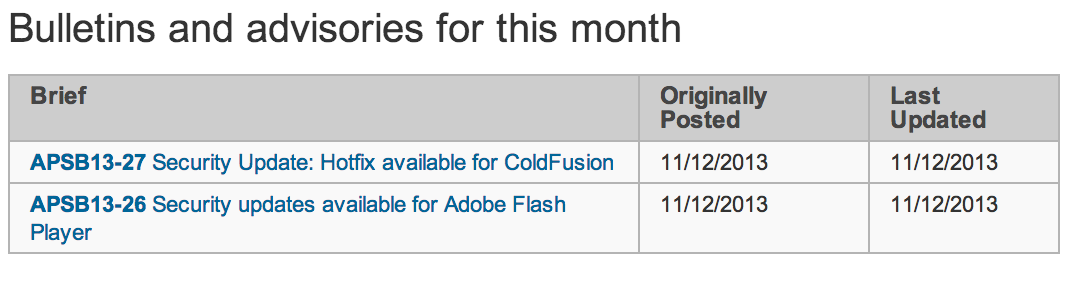
Today, Adobe released two security bulletins describing vulnerabilities in Flash Player and ColdFusion. A remote attacker could exploit the worst of these flaws to gain complete control of your computer. The summary below details some of the vulnerabilities in these popular software packages.
- APSB13-26: Four Flash Player Memory Corruption Flaws
Adobe Flash Player displays interactive, animated web content called Flash. Many users install Flash, so it’s likely present on many of your Windows and Mac computers.
Adobe’s bulletin describes two unspecified memory corruption vulnerabilities in Flash Player running on all platforms. Though the flaws presumably differ technically, they share the same scope and impact. If an attacker can lure you to a web site, or get you to open a document containing specially crafted Flash content, he could exploit these flaws to execute code on your computer, with your privileges. If you have administrative or root privileges, the attacker could gain full control of your computer.
Adobe assigned these flaws their highest severity rating for Windows and Mac computers, but a lesser severity for Linux machines.
Adobe Priority Rating: 1 for Windows and Mac (Patch within 72 hours)
- APSB13-27: Two ColdFusion Vulnerabilities
Adobe ColdFusion is an application server that allows you to develop and deploy web applications. It suffers from two security vulnerabilities, which Adobe does not describe in much technical detail; a reflected cross site scripting (XSS) vulnerability (CVE-2013-5326), and an unauthorized remote read access flaw (CVE-2013-5328). Other than that, the bulletin shares very little about the scope or impact of these flaws, so we’re unsure how easy or hard it is for attackers to leverage them. Presumably, if an attacker could trick someone in clicking a specially crafted link, he could leverage the XSS flaw to do anything on your web site that the user could. We also assume an attacker could exploit the remote read flaw to potentially gain access to files on your server, such as its web application source code. In any case, they rate the vulnerabilities as Priority 1 issues for version 10, which is their high severity rating.
As an aside, Adobe’s own network was recently breached via a zero day flaw in ColdFusion. Adobe claims these ColdFusion issues are not associated with their network breach. However, the discoverer of one of the issues, Alex Holden, was actually one of the researchers who uncovered Adobe’s data breach, and he claims one of the flaws has been used by attackers this year to break into other companies. In other words, you should apply these updates immediately if you use ColdFusion
Adobe Priority Rating: 1 for version 10 (Patch within 72 hours)
Solution Path:
Adobe has released updates for all their affected software. If you use any of the software below, we recommend you download and deploy the corresponding updates as soon as possible, or let Adobe’s automatic updater do it for you:
- APSB13-27: Apply the corresponding ColdFusion hotfix. More details in this Adobe technote.
- APSB13-26: Upgrade to the latest Flash Player (11.9.900.152 for Windows)
For All WatchGuard Users:
Attackers can exploit these flaws using diverse exploitation methods. However, WatchGuard’s XTM appliances can help in many ways. First, our IPS and AV services are often capable of detecting the malicious Flash or Shockwave files attackers are actually using in the wild. If you’d like, you can also configure our proxies to block Shockwave or Flash content. This, however, blocks both legitimate and malicious content. If you do want to block this Flash or Shockwave via the Web or email, see our manual for more details on how to configure our proxy policies’ content-filtering.
Status:
Adobe has released patches correcting these issues.
References:
This alert was researched and written by Corey Nachreiner, CISSP (@SecAdept)


“If you just look at the heel, you are immediately going to see that if there was not the (right) engineering), it would break,” the designer told CNN
parajumpers kodiak women
Some of the information in this article is incorrect.
“Adobe’s own network was recently breached via a zero day flaw in ColdFusion.”
To my knowledge, Adobe has not publicly released the attack vector used to breach their network. While the breach leaked the source code for CF, there is no current indication that a CF vuln was used in the breach. Many people have jumped to the same conclusion you have. If you have an official account from Adobe that names the attack vector as CF, please list it, otherwise, please remove the incorrect information from this article.
“Alex Holden, was actually one of the researchers who uncovered Adobe’s data breach, and he claims one of the flaws has been used by attackers this year to break into other companies. ”
In regards to the specific CF security bulletin listed in this article, Adobe has announced that there are no reports of the vuln being used in the wild. In fact, the vuln Adobe fixed is purported to be unrelated to what Holden reported, but they uncovered it while researching a report from Holden. Furthermore, Holden did _not_ report that attackers were “breaking into” companies– they simply reported what they believed to be patterns of a hack attempt on a server and acknowledged that they are “Unaware of the possible effectiveness of this attack” and that “Adobe did not find the precise attack effective against any of supported CF versions”. Please see additional information here and update your article.
http://krebsonsecurity.com/2013/11/zero-days-rule-novembers-patch-tuesday/
It is important for the new patch to be installed, but it is not known to be exploited in the wild, nor was it reported by Holden.
Thanks!
~Brad